A minimal checklist for hardening (securely configuring) and optimization of a WordPress…
The Role of Business in Cybersecurity
This article discusses the role of Business in Cybersecurity and how they can assess the security level of IT/OT systems they own. Because the Business must participate in the overall cybersecurity program of the organization, it should not delegate overall responsibility for the cybersecurity of the IT/OT systems it owns (existing or to be implemented) to technical personnel.
Introduction
Fearful of the growing number of publicly disclosed cybersecurity attacks and incidents, Business personnel are increasingly asking their Technical colleagues an ostensibly simple question, expecting a simple answer: “How secure is this IT system?”.
The Business already knows that this question is rhetorical, that the answer is not as simple as they expect, and that asking it is the source of frustration and tension with the Technical staff. But the Business keeps asking, and the organization frequently does nothing to make it easier the next time.
This article is intended for Business people and I’ll try to respond to their seemingly rhetorical and straightforward question using their language and providing them with some good food for thought.
“Word to the wise” for those in the technical field.
Cybersecurity Metrics for Business
To appropriately respond to the question “How secure is this IT system?” both the questioner and the responder must first define a common metric for measuring the cybersecurity level of an IT system.
In other words, both the questioner and the respondent must put themselves in the same situation when asking and responding to the question “How long is the way?” in which both have in mind an implicit metric (e.g., metric system, imperial system). Having a pre-defined and common metric eliminates any ambiguity in such questions and answers, enables accurate and timely measurement (and responses), and avoids potential frustrations and conflicts between parties.
The Cybersecurity Risk Metric, which looks like the model depicted in Figure 1 in a simplified but helpful way to achieve the objectives of this discussion, is a metric for measuring the security of an IT system and then responding to or question “How secure is this IT system?”
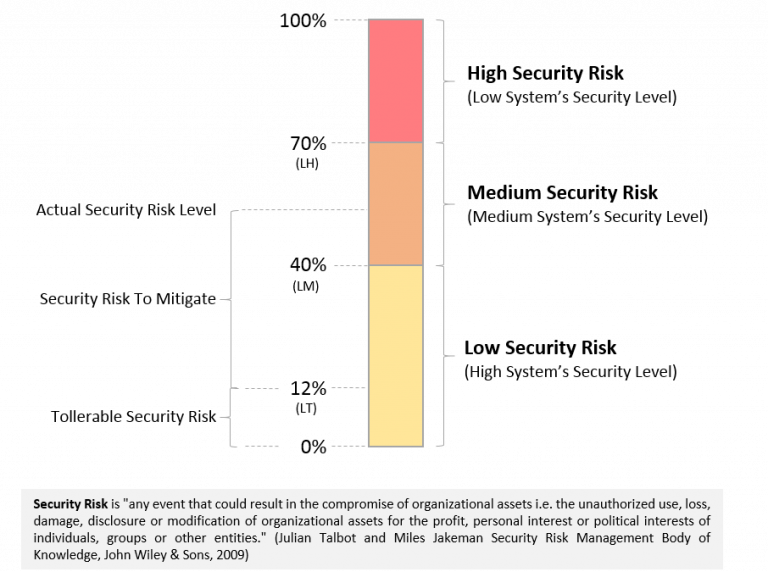
Figure 1 – Cybersecurity Risk Metric (Security Level) model for Business.
The Cybersecurity Risk Metric allows measuring the actual cybersecurity risk exposure level (“system’s security level”) of an existing IT system or defining the maximum expected cybersecurity risk level of a new IT system to be implemented, as well as identifying the cybersecurity controls to implement into the IT system in order to reduce the cybersecurity risk exposure to its actual level to the expected level. Cybersecurity risk measures can be quantitative (e.g., from 0 to 100) or qualitative (e.g., high, medium, low).
The Role of Business in Cybersecurity
Figure 1 depicts some considerations that Business (and Technical) personnel in an organization should keep in mind when defining the Cybersecurity Risk Metric or measuring the cybersecurity level of an IT system:
- Each security event, or class of security events, or security characteristic (confidentiality, integrity, availability) of a system can have its own Cybersecurity Risk Metric. To make the original question “How secure is this IT system?” more understandable and measurable, it should be reformulated as “How secure is this IT system against unauthorized access?” or “How secure is this IT system in terms of the confidentiality of the information it manages?” or “How secure is this IT system in terms of remaining operational even in the face of hardware failure?”.
- Because achieving zero cybersecurity risk is not possible, the Business (not the Technical people) must define a maximum tollerable security risk (LT) for each Cybersecurity Risk Metric while keeping in mind that it is proportional to the cost that must be spent to achieve it. Lower tollerable risk implies higher costs for implementing the security controls required to achieve it. The activity required to reduce an IT system’s actual security risk to the tolerable security risk is known as risk mitigation, and the associated costs are known as risk mitigation costs. It is worth noting that security risks can be reduced not only through technical measures, but also through the combination of technical measures and cybersecurity insurance (a topic I will address in another article).
- The security risk threshold (LH, LM, LT) should vary depending on the business criticality of the IT system in order to strike the right balance between cybersecurity level and cost to implement and operate it. For example, the IT system that manages end-of-year gifts to employees should have much higher thresholds (LH, LM, LT) than the IT system that generates client bills and collects revenue. If the first system fails due to a security incident, the organization can perform the same task manually or wait for the system to be repaired. If the second system fails, the job cannot be completed manually, and the organization risks losing money and its reputation, as well as facing regulatory or legal consequences.
- To simplify cybersecurity implementation and measurement, an organization can define its own standard Cybersecurity Risk Metrics, as well as security risk thresholds for each, based on the business criticality of the IT system. As a result, when the Business requests the implementation of a new IT system, the Technical staff is already aware of the minimum expected cybersecurity compliance level. Furthermore, the original question “How secure is this IT system?” can be phrased more simply as “Is this IT system compliant with our cybersecurity standard?”.
Based on these considerations, the Business in an organization should not delegate all cybersecurity activities to their Technical colleagues, but should instead play a key role in defining the Cybersecurity Risk Metrics so that they are fully aware of how well IT systems they own are protected against cybersecurity threats and how much budget they should set aside to mitigate the actual security risk to the maximum tolerable security risk (security risk to mitigate).
When the Business plays this role, they will correctly rephrase the initial question (“How secure is this IT system?”) and will be able to pretend and comprehend a more precise and quick response. Their technical colleagues, on the other hand, should understand that cybersecurity is primarily a business matter, that should not be used for political purposes within the organization, and that they should make every effort to ensure that the Business is involved in defining the organization’s cybersecurity standards, that the Business provide the cybersecurity requirements for the IT systems they own, and that both of them are perfectly aligned.
Cybersecurity is Managing Security Risks (not only Penetration Testing)
Many Business personnel have a clear understanding of what a penetration test or a vulnerability assessment is and they are confident that if the IT systems they own pass these tests/assessments, these systems are “secure”. However, this is not the case because a penetration test ([2] [3] authorized simulated cyberattack on an ICT system – also known as a pen test, pentest, or ethical hacking) can only evaluate a portion of the system’s security.
Let’s look at an example. An organization’s Customer Information System is managed by an untrustworthy system administrator who has access to all of the company’s customers’ data and sells it to the competition. Because of the system administrator’s role, he or she has default access to this system and data, and a penetration test is ineffective in identifying this security risk.
Cybersecurity is thus more than just penetration testing; it is a process for managing security risk throughout an IT system’s lifecycle, and it includes many sub-processes such as security risk identification, analysis, evaluation, and treatment (mitigation). Cybersecurity Metrics, as previously described, play a key role in this process and its sub-processes, as do Business personnel.





Comments (0)