A minimal checklist for hardening (securely configuring) and optimization of a WordPress…
Knowledge From Security Vulnerabilities
Security vulnerabilities can provide valuable knowledge for business, technical and operational decision-making and Vulnerability Intelligence is the practice to determine such information and knowledge. Computer system security vulnerabilities [1][2] are dangerous and must be addressed because they can be exploited to compromise the confidentiality, integrity, and availability of computer systems, as well as the data and information stored and managed by these systems. The analysis of security vulnerabilities, on the other hand, can serve as a valuable source of information and knowledge, and we can refer to this as Vulnerability Intelligence. In this article, I’ll introduce the fundamental concepts of Vulnerability Intelligence, its components, and two case studies to demonstrate the benefits these systems can bring to an organization’s decision-making processes.
Knowledge From Security Vulnerabilities - Definition And Benefits
Vulnerability Intelligence is a set of mathematical models, analysis methodologies, processes, and technologies to get knowledge from security vulnerabilities, as well as other data sources, that can be used in cybersecurity business, technical and operational decision-making processes.
Vulnerability Intelligence offers the following benefits and values:
- Make timely, accurate, effective, and evidence-based cybersecurity business and operational decisions.
- Increase the level of cybersecurity while reducing the time and effort required to achieve it.
- Reduce the overall complexity and cost of vulnerability management and remediation processes.
- Improve the effectiveness of “security by design,” as well as the identification of technologies, people (e.g., developers, vendors), and processes on which to focus in order to increase cybersecurity.
- Relax any potential tensions that may exist between various organizational roles as a result of the overhead and delay required by vulnerability management.
Data vs. Information vs. Knowledge
Organizations’ information systems have accumulated massive amounts of cybersecurity vulnerabilities and organizational data from both internal and external sources. Even if this data is formally and standardized collected and stored, it is primarily used for cybersecurity vulnerability remediation and cannot be used directly for other decision-making; instead, it must be processed using appropriate extraction tools and analytical methods to transform data into actionable information and knowledge for decision-makers.
- Data, in general, is a structured codification of single primary entities as well as transactions involving two or more primary entities. Data examples include the results of automated cybersecurity vulnerability assessments, cybersecurity incidents, computer system and network configurations, and the organization’s structure.
- Information is the result of data extraction and processing activities, and it appears meaningful to those who receive it in a specific domain. Examples of data transformed into information include cybersecurity vulnerabilities that must be fixed based on real security risk rather than severity, technologies, and processes that lead to the majority of cybersecurity vulnerabilities and development teams that produce more secure and high-quality software.
- Knowledge is information that has been transformed and is used to make decisions and develop actions. As a result, we can think of knowledge as information applied to a specific domain, augmented by decision-makers’ experience and competence in tackling and solving complex problems. Examples of information transformed into knowledge include the root causes of cybersecurity vulnerabilities (organization, people, processes, and technologies), the effectiveness and adoption of cybersecurity policies and procedures, cybersecurity training and awareness sessions provided within the organization, and the prediction of cybersecurity vulnerability remediation time based on historical data.
Knowledge From Security Vulnerabilities - Building Blocks
Vulnerability Intelligence, like business intelligence, allows users to get knowledge from security vulnerabilities as well as other data sources using the building blocks represented in Fig. 1.
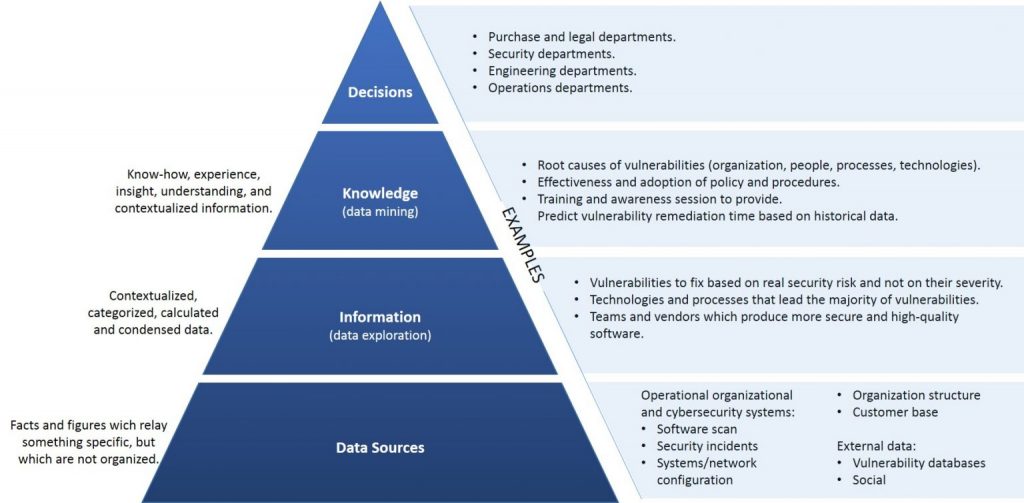
- Data Sources – The first level of the pyramid (bottom) necessitates the collection and integration of data from a variety of primary and secondary sources of varying origin and type. The sources are primarily data from cybersecurity operational systems, but they may also include structured or unstructured organizational data, as well as data from third-party providers. The data from these data sources is loaded and stored in a database (data warehouse) designed to support Vulnerabilities Intelligence analyses, and it is used to feed mathematical models and analysis methodologies that aid decision-makers.
- Data Exploration (transform data into information) – At the second level of the pyramid, there are the tools used to conduct a passive Vulnerability Intelligence analysis, including query and reporting systems and statistical methods. These are called passive methodologies because decision-makers are asked to generate prior hypotheses or define data extraction criteria before using analysis tools to find answers and confirm their original insight. As a result, they may wish to test their hypothesis using extraction and visualization tools, followed by a statistical test to ensure that data adequately support their conclusions.
- Data Mining and Optimization (transform information into knowledge) – The third level of the pyramid contains active Vulnerability Intelligence methodologies for extracting knowledge from information, as well as optimization models for selecting the best solution from a set of alternative actions. These include mathematical models for pattern recognition, machine learning, and data mining techniques. Active models, unlike the tools described at the data exploration level, do not require decision-makers to develop any prior hypotheses to be validated later. Instead, they want to expand the decision-makers’ knowledge.
- Decisions – Finally, the top of the pyramid represents the choice and actual adoption of a specific decision, and thus the natural conclusion of the decision-making process. Even when Vulnerability Intelligence methodologies are available and successfully implemented, decision-making is left to the decision-makers, who may also use informal and unstructured data to adapt and modify the recommendations and conclusions reached through mathematical models.
Vulnerability Intelligence provides increasingly sophisticated active support tools from the bottom to the top of the pyramid. Roles and competencies shift as a result. The required competencies are primarily provided by the organization’s information systems specialists, who are located at the bottom of the pyramid (e.g., cybersecurity experts). Analysts and experts in mathematical and statistical models supervise the intermediate phases. Finally, the activities of decision-makers in charge of the application domain are dominant at the top.
Knowledge From Security Vulnerabilities - Case Studies
Case Study 1 – Cybersecurity Vulnerabilities Reprioritization
SUBJECT: Reduce and/or reprioritize the application vulnerability to fix. RATIONALE: The majority of organizations today request that software application vulnerabilities be fixed based on their severity rather than their actual potential exploitability in their ICT environments. If a software application is protected by an application firewall, for example, the true number of exploitable cross-site scripting vulnerabilities is less than the number currently counted. As a result, the fix for such vulnerabilities can be reprioritized or even declared false positive, freeing up time and effort to fix vulnerabilities that are truly more dangerous. DATA SOURCES: A) Database of cybersecurity vulnerabilities discovered in the organization’s software applications during the implementation life cycle. B) Database of incidents caused by application vulnerabilities discovered by the organization during application operation. RESULT: The dashboard in Figure 2 displays the current and new severity levels of cybersecurity vulnerabilities affecting the organization’s software applications.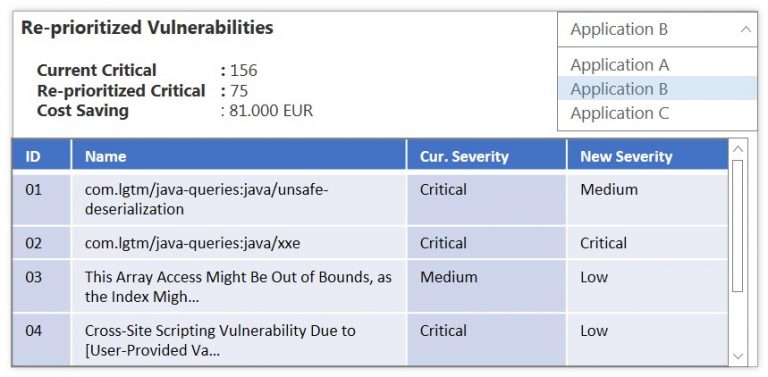
Case Study 2 – Software Development Teams Performances
SUBJECT: Measuring the performance of development teams based on the density of software vulnerabilities. RATIONALE: A high vulnerability density (number of vulnerabilities/lines of code) has unfavorable consequences such as delays in software delivery and deployment, increased project costs due to fix activities, and the risk of having to redesign a portion of the application. Knowing the average vulnerability density for each development team could lead the organization’s management to assign the development of business-critical applications to the best performers and plan secure coding training sessions for the worst performers. DATA SOURCES: Database of vulnerabilities discovered in the organization’s software applications during the implementation life cycle. RESULT: The dashboard in Figure 3 displays the average vulnerability density for each development team.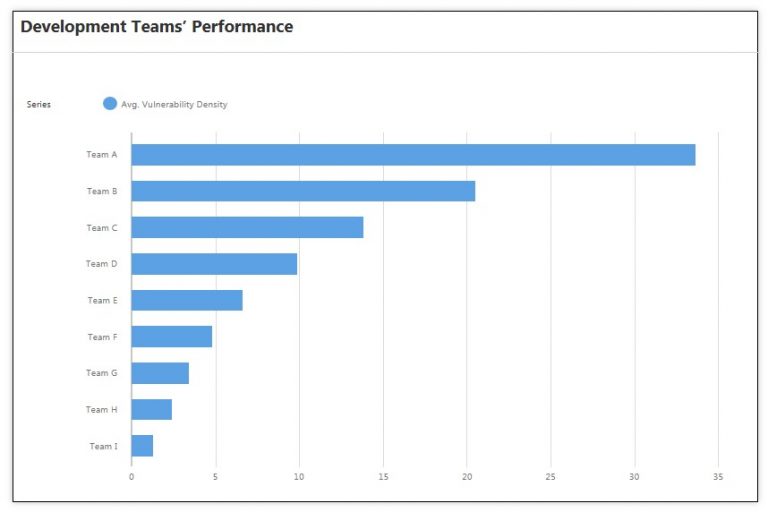
Conclusions
Vulnerability Intelligence extracts valuable information and knowledge for decision-making from cybersecurity vulnerability data, which is often only used for remediation. It is possible to generate information and knowledge that can be used in complex cybersecurity decision-making processes using a set of mathematical models, analysis methodologies, processes, and technologies that use primarily an organization’s cybersecurity vulnerabilities data, as well as other data sources.
References
[1] Software Security, Andrea Desantis, 2020
[2] Software Security Vulnerabilities, Andrea Desantis, 2021
[3] Business Intelligence: Data Mining and Optimization for Decision Making, Carlo Vercellis, Politecnico di Milano – Italy, 2009.





Comments (0)